%20Wie%20funktioniert%20sie.jpg)
Digital signatures are available in various forms - from simple electronic signatures (EES) to advanced electronic signatures (FES) and qualified electronic signatures (QES). Each variant fulfills its own legal and technical requirements. The advanced electronic signature occupies an important intermediate position: it makes it possible to digitally sign the document in a legally secure manner without losing time or having to go through complicated technical processes. This glossary article shows how the FES works, what advantages it offers and in which areas of application it is useful for companies and private individuals.
The advanced electronic signature, known as Advanced Electronic Signature (AES), is a digital signature that is suitable for various contracts. It combines a high level of security with a simple and efficient application, which makes it particularly practical for everyday business processes. What sets FES apart is its ability to unambiguously verify the identity of the signatory without having to resort to complex procedures. Thanks to uncomplicated authentication methods, the signature process remains fast and user-friendly, while at the same time ensuring a high level of security. Typical authentication methods such as SMS-TAN or e-mail verification are described below.
The FES is particularly impressive due to its practicality. It can be implemented quickly and is easy to use, as identification is usually carried out using common methods such as email confirmation or SMS TAN. As a result, documents can be signed quickly and approval processes accelerated.
Another advantage is the simple integration into existing digital workflows. Contracts, approvals or internal guidelines can be signed directly in one system, without cumbersome intermediate steps or delays. At the same time, the FES remains recognized throughout the EU and thus offers legal certainty for numerous business transactions. Thanks to its security, flexibility and ease of use, FES is particularly attractive for companies that regularly process contracts digitally.
The qualified electronic signature (QES) is legally regarded as the strongest form of digital signature. It is required by law in certain cases, for example in notarial processes or in employment law, when a written form is mandatory. In order to meet the high security requirements, QES requires particularly strict identification, which is often carried out via certified trust centers, video identification procedures or hardware security modules. As a result, it offers maximum legal protection, but is also associated with greater effort and additional costs.
The advanced electronic signature (FES) is less complex to use and has fewer requirements, but still offers a high level of security. It is usually based on two-factor authentication, for example by e-mail confirmation or SMS code, and does not require any special end devices. FES is suitable for cases where security and authenticity are required, but the high requirements of QES are not necessary.
Companies can therefore decide flexibly in which scenarios the FES offers sufficient security and when the QES is mandatory for legal reasons.
The legal basis for electronic signatures in the EU is the eIDAS Regulation (EU No. 910/2014). It defines three levels: the simple, the advanced and the qualified electronic signature. For the advanced signature (FES), the regulation describes specific requirements that ensure its security and legal validity.
These include:
Thanks to these requirements, the FES offers a high level of security without compromising on flexibility and user-friendliness. It is an efficient solution for companies and private individuals to sign digital documents quickly and securely.
The advanced electronic signature offers a high level of security, in particular through the ability to uniquely identify the signatory. Various authentication methods can be used, depending on the solution or requirement. In this way, the signature remains clearly assignable, while the process remains simple and understandable.
The most common identification methods are as follows:
These authentication procedures ensure that the signature process remains secure and reliable without increasing complexity.
The advanced electronic signature (AES) is legally binding and offers a significantly higher level of security than the simple electronic signature (EES). While the EES often has little probative value, as it can only be created by a scanned image of a signature, the identity of the signatory is verified with the AES. In addition, a digital certificate is stored that secures the signature and makes any changes to the document traceable. This gives the FES a much stronger indication of who has signed a document and its validity is generally difficult to dispute.
The advanced electronic signature is used in situations where a high degree of legal security is required, but no legally required handwritten signature is necessary. It enables the signatory to be clearly identified and thus strengthens the probative value in the event of a dispute. At the same time, it protects the integrity of the document, as subsequent changes would be clearly recognizable. This makes the FES particularly suitable for contracts where tamper-proofing and traceability are paramount.
Typical areas of application include:
Insurance documents, such as life, accident and disability insurance policies, which are not subject to the strict requirements of money laundering laws.
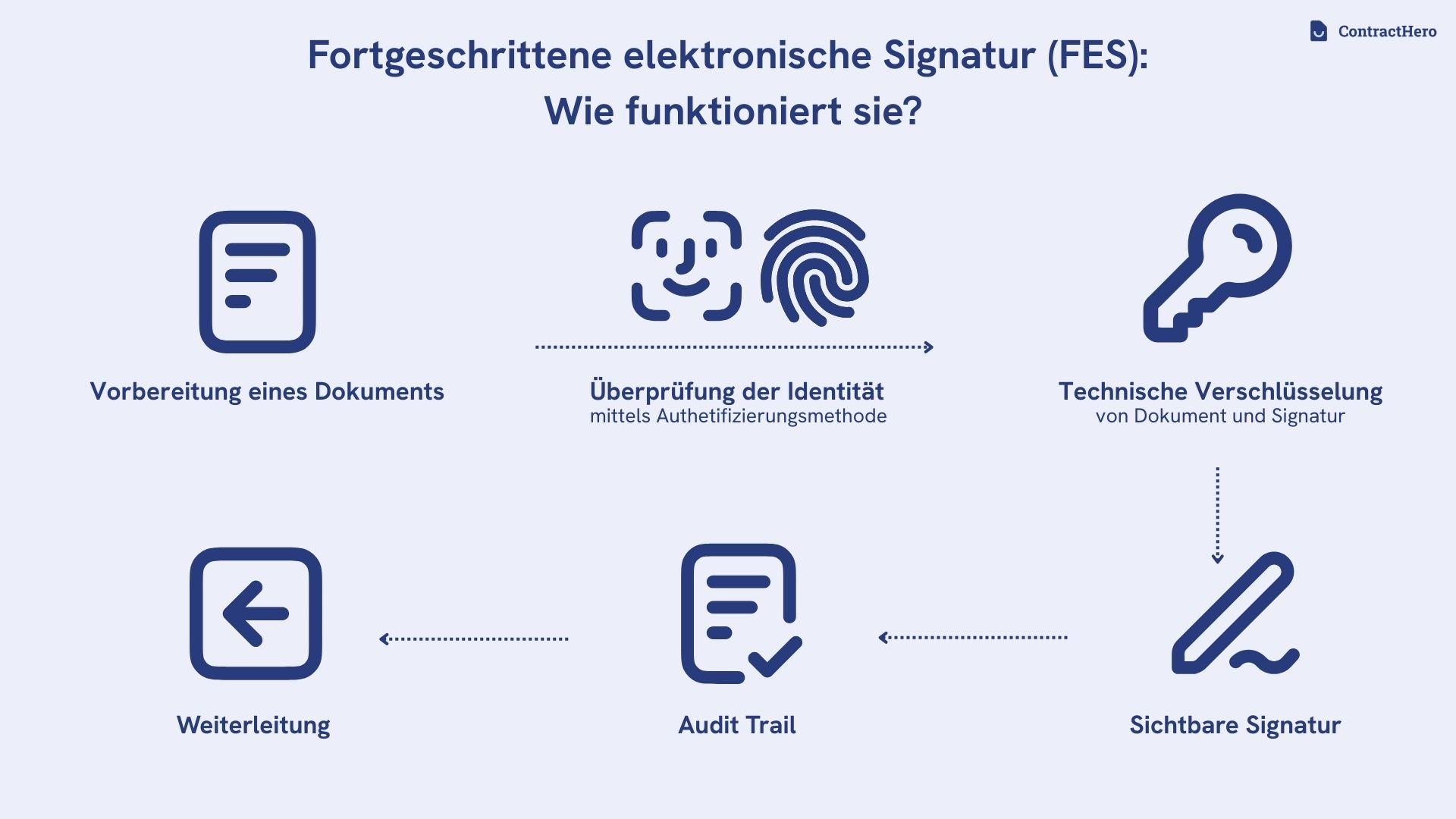
An advanced electronic signature (AES) is created using special signature software that technically secures the entire process. This ensures that the signed document remains unchanged and is legally binding. The process consists of just a few steps and is easy to understand for both companies and private individuals:
1. prepare document
The desired document is uploaded to the signature software. There it is prepared for the signature process.
2. identity check
To ensure that the signature can be clearly assigned to the signatory, the identity is verified. This is often done using a simple authentication method, such as verifying a cell phone number. The signatory receives an SMS code that confirms that the signature is legitimately assigned to this person.
3. technical encryption
In the background, the software encrypts the document with a unique signature key. This is an individual code that is only valid for this signature process and uniquely links the document to the signature, while a hash algorithm generates a unique character string so that any subsequent changes to the document would be immediately recognizable.
4. visible signature
The signatory often inserts an image of the signature, which gives the document a visual signature. However, this image is only used for visualization and has no legal significance. The actual, legally binding part of the signature is the digital encryption in the background.
5. Audit Trail
In addition, an audit trail is created that fully documents the entire signature process. This audit trail contains all relevant information - from the authentication of the contracting party to the linking of the signature with the document, making the FES and its process traceable and contractually secure at all times.
6. dispatch of the document
After successful signing, the encrypted document is forwarded to the recipient together with the certificates. These certificates enable the recipient to verify the authenticity and integrity of the signature.
The fields of application for electronic signatures are diverse and extend across various sectors.
The FES is a practical solution, especially for business transactions with a medium liability risk. However, as soon as the law requires the written form, the qualified electronic signature (QES) is mandatory. It offers the highest level of security and the strongest legal effect. In addition, it can also be useful in particularly important business cases, for example to secure critical contracts such as company acquisitions, large financing agreements or long-term license and supply agreements
The advanced electronic signature (FES) is an efficient solution for the legally secure digital signing of documents. It meets the requirements of the eIDAS Regulation, provides clear identification of the signatory and protects documents from tampering. For business transactions with a medium liability risk - such as contracts, non-disclosure agreements or insurance documents - the FES is therefore practical, recognized and flexible to use.
ContractHero supports companies with contract management software that integrates both FES and QES. All signatures are fully eIDAS-compliant and are secured by the highest security standards - in accordance with ISO 27001 certification. ContractHero thus combines the advantages of digital signatures with structured and efficient contract management.